Focuses on configuration review and risk associated with your On-Premises Security Infrastructure components.
Approach
On-Prem Configuration Review
Security configuration review of network and security appliances such as firewalls, intrusion detection systems, proxy filters.
Standards Benchmarking
Benchmarking against organization configuration standards and/or industry frameworks such as ISO2701, NIST, CIS controls, PCI-DSS.
Scope of Assessment
-------
Network Firewalls Policy Review
- Unnecessary Ports
- Insecure Rules
- Secure Configuration
Intrusion Detection Systems Policy Review
- Traffic to Command and Control Systems
- Rogue Outbound Traffic
- Traffic Anomalies
- Performance Optimization
Privilege Management Systems Configuration
- Discovery of Service Accounts
- Management of Privileged Entitlements
Data Loss Prevention System Policy Review
- Data Classification
- Detection for Data Leaks
- Sensitive Information Leaks
- Intellectual Property Leaks
Proxy Filter Rules Review
- Web Filtering for Authenticated Users
- Unauthenticated Access Permissions
- Performance Optimization
Value Proposition
-------

-

Report of Configuration issues and Risks Observed
-

Remediation Strategy
-

Benchmarking Comparison Report
-

Hardening Standards Report
-

Risk Score
External facing assets are most vulnerable, and we view and think from a hacker’s perspective to identify these vulnerabilities and risk associated.
Approach
Exterior Analysis
Perform non-intrusive scans on external facing entities of your organization from outside of your environment.
Deep/Dark Web Analysis
Monitor dark web for information related to your organization.
Cloud Surface Analysis
Monitor external facing cloud services to identify insecure configuration
Scope of Assessment
-------
HackView LENS is a suite of tools and utilities used to perform around 50 checks at different layers of your web presence to identify issues.
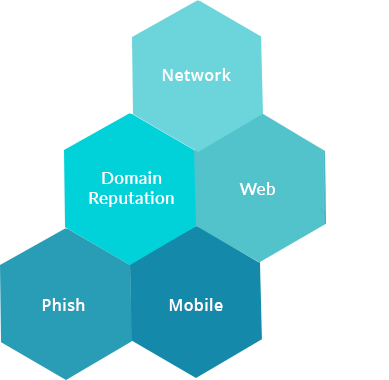
HackView Network LENS
Identify insecure network services and misconfigurationsHackView Phish LENS
Discover CyberSquatting, TypoSquatting and Potential Phishing DomainsHackView Mobile LENS
Static analysis of Android APK to find vulnerabilities and code compliance issuesHackView Web LENS
Identify insecure software versions, web misconfigurationsDomain Reputation LENS
Detect SSL/TLS issues, insecure ciphers, Blacklisted IPs, URLs and identify misconfigurations on SPF, DMARC, DNS Health Records AssessmentsHackView Credential LENS
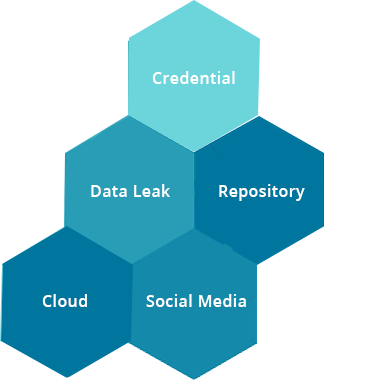
Discover breached credentials in dark web and in false campaignsHackView Data Leak LENS
Discover sensitive information, Intellectual Property leaks in Surface Web and Dark WebHackView Repository LENS
Discover leaked Secrets, Keys, APIs, credentials in GitHub and BitbucketHackView Cloud LENS
Discover leaked S3 buckets and misconfigurations on Cloud ServicesHackView Social Media LENS
Research Malicious and Brand Reputation related conversations, potential attacksValue Proposition
-------

-

Report of Configuration Issues and Risks Observed
-

Remediation Strategy
-

Risk Score
Focuses on identifying vulnerabilities on organization’s on-prem and cloud network infrastructure and attempt to exploit them. This helps in identifying threats and plan to mitigate them before the bad actors act on them.
Approach
Network VAPT
Perform network vulnerability assessment of internal and external network infrastructure on both On-prem and Cloud to identify sucurity flaws.
Penetration Testing
View the network through the eyes of a hacker to exploit the vulnerabilities and attempt to breach the network.
Threat Assessment
Assess the threats associated with the vulnerabilities and breaches observed.
Scope of Assessment
-------
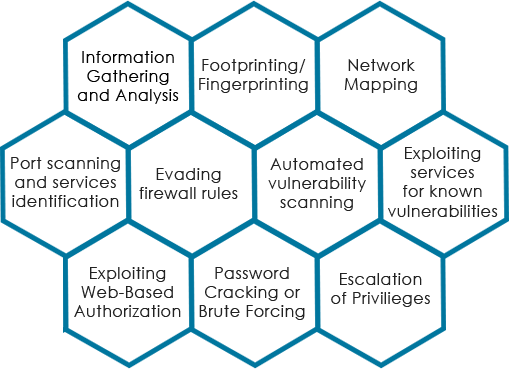
We perform the Vulnerability Assessment and Penetration Testing on your network infrastructure

We perform the Penetration Testing to cover the below categories
Value Proposition
-------

-
 Report of Exposed Vulnerabilities & Threats on the Network
Report of Exposed Vulnerabilities & Threats on the Network -

Information of Required Patches
-

Report of Assets Breached
-

Remediation Strategy
-
 Security Posture Improvement Techniques
Security Posture Improvement Techniques -

Risk Score