Focuses on identifying vulnerabilities on your Applications hosted On-Premises/Cloud and attempt to exploit them.
Approach
Aplication Vulnerability Assessment
Perform application vulnerability assessments on the applications to identify security flaws.
Penetration Testing
Discover exploitable vulnerabilities in web applications and attempt to compromise them. Performed as per OWASP and SANS standards.
Threat Assessment
Assess the threats associated with the vulnerabilities and breaches observed.
Scope of Assessment
-------
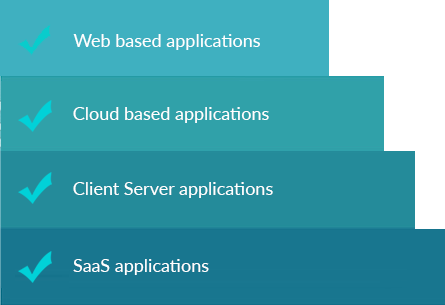
We perform the Vulnerability Assessment and Penetration Testing on the Applications

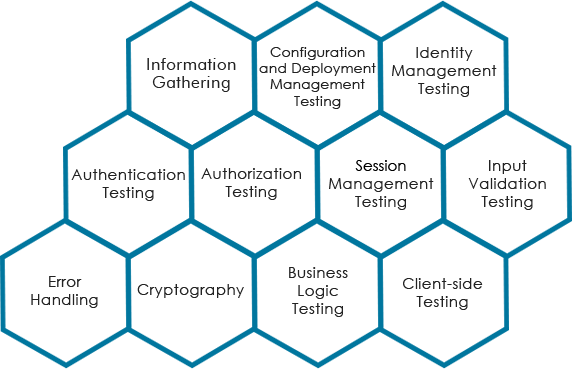
We perform the Penetration Testing to cover the below OWASP categories
Value Proposition
-------

-

Report of Exposed Vulnerabilities & Threats on the Applications
-

Prioritized Findings
-

Report of Assets Breached
-

Information of Required Patches & Remediation Strategy
-

Security Posture Improvement Techniques
-

Risk Score
Focuses on collaborating with your internal teams to understand the architecture of the applications and provide end-end security assessment to ensure best practices are met and security controls in place.
Approach
Engange & Collaborate
Engage during the application development lifecycle (preferably) of even after the application development.
Collaborate with application and enterprise architects to design security.
Evaluate amd Implement
Evaluate individual application components of and data flows to ensure security policies are met.
Develop and implement information security stategies during the application development lifecycle.
Risk Assessment
Identify threats and vulnerabilities that impact the applications some of which are not identified with typical VAPT.
Access risks caused by the threats and the vulnerabilities observed.
Controls Assessment
Identify the controls in place and their effectiveness to mitigate the risk.
Ensure the controls conform with organization’s security policy and NIST standards 800-37, 800-30, 800-39.
Scope of Assessment
-------
We perform End-End Risk Assessment on
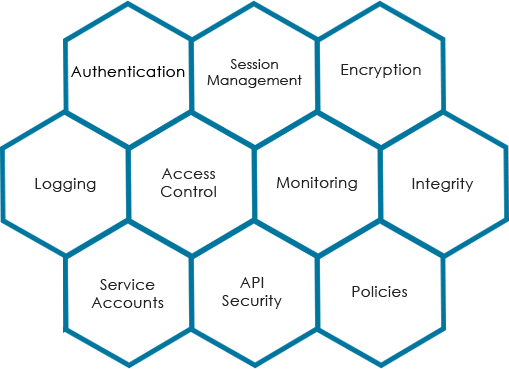
We cover various areas to understand the application architecture to assess the risk
Sample Assessment Review
-------
The assessment process identifies the gaps in the architecture and help the application and architecture teams to design security during the development lifecycle.

Questions to Ponder
- Where is the SSL certificate terminated (on load balancers or web servers)?
- Is PII information displayed or masked on the web interface?
- What is the max session timeout configured on the application?
- Can you create local accounts on the application?
- Where are the passwords stored?
- Is there logging enabled?
- Are passwords hashed?
- Are there any default accounts on the application?
Value Proposition
-------

-
 Report of Vulnerabilities & Threats associated with the Applications
Report of Vulnerabilities & Threats associated with the Applications -
 Report of Risks Identified and Mitigation Controls
Report of Risks Identified and Mitigation Controls -
 Assess Residual Risk and provide Risk Mitigation Strategy
Assess Residual Risk and provide Risk Mitigation Strategy -

Risk Score
